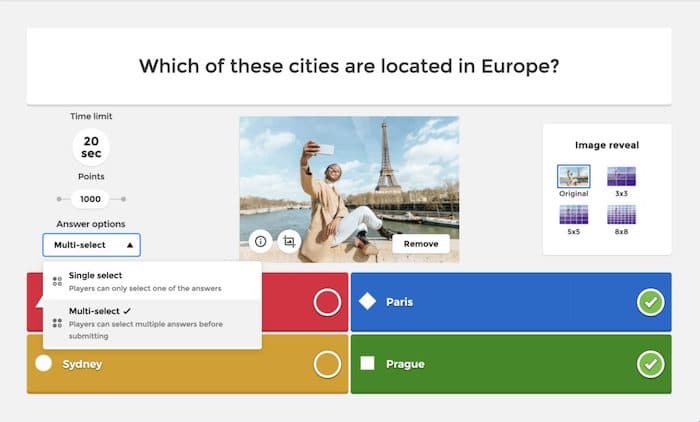
There are many indicators to deciding whether it is time to onboard an MSP. Some businesses find they are struggling to keep up with updates and network management, placing their systems at risk for outages or breaches. Or perhaps you’ve found that your internal IT team is struggling to keep up with demand, resulting in a reactive approach rather than a proactive one. No matter what your current needs are, here are some signs you may be ready to onboard an MSP.
1: You don’t have a cyber security policy or strategy
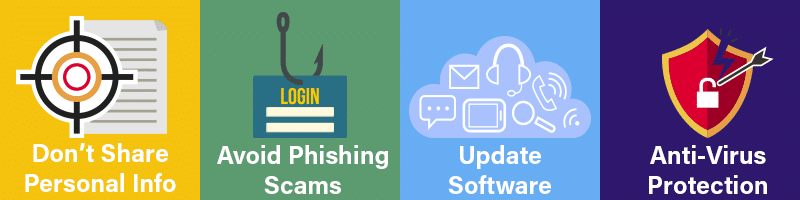
Cyber security threats are on the rise, so it is absolutely essential that businesses have a solid and effective cyber security strategy in place. An MSP can design a custom risk mitigation strategy for your company using the latest cyber technology and will continue to monitor and update your systems for threats.
2: You have regular downtime
If you are having regular downtime due to systems crashing, software lags, or simply needing to search for a solution to minor IT issues, then it’s a serious sign that you may need to outsource some of your IT. Just one hour of downtime can cost up to thousands of dollars, and in the long run this is just plain uneconomical. An MSP can restructure your IT so it is efficient and streamlined and will monitor your systems to prevent issues from occurring before you get the chance to notice them.
3: Inefficient support
As your business grows, the complexity of your IT systems grows with it. This can cause issues for inhouse IT staff, who may want to focus on important IT projects but find themselves falling behind as they struggle to keep up with demand for support internally. Additionally, as technology evolves your in-house team may lack the knowledge to effectively fix IT problems that they have no experience in.
MSPs are constantly keeping up with the latest technologies, thus they have the ability and knowledge to answer queries and provide support when needed so your IT team can focus on more important projects. With just one click or call, your MSP is available to provide onsite or remote assistance to quickly resolve issues.
4: No backup plan
Having no backup plan means that in the event of a system outage, black out, or ransomware attack, all of your data could be lost. It is essential to have multiple backups of your data in both the cloud and on a hard drive, otherwise you risk losing your data and compromising its security. This can be devastating for a business of any size.
An MSP can devise a safe and secure backup strategy and monitor it both in the cloud and on a physical copy.
5: Need for technical expertise
With so many new software and applications being brought out, it can be difficult to keep up with your subscriptions or decide what is suitable for your business. There are a multitude of apps and technology that can help drive business growth, but it can be difficult to discern which are fads. Alternatively, perhaps you are finding that your current software is no longer able to keep up with your business operations.
MSPs are knowledgeable on all the latest software and apps. They can assess your needs and requirements to determine which applications can drive your business forward and assist with its continued growth.