Regular Backups
Hi everyone, and welcome to the final episode of eight weeks of the essential eight! In this episode we’ll be discussing regular backups, why they’re considered essential, and how you can achieve maturity level one. Let’s begin!
The ACSC defines this strategy as: Regular backups of important new/changed data, software, and configuration settings, stored disconnected, retained for at least three months. Test restoration initially, annually, and when IT infrastructure changes.
Why regular backups?
If the mitigation strategies you have meticulously put in place fail, or things go completely sideways due to a catastrophic event, backups are vital for the continuation of your business operations.
Data and files have always been the backbones of businesses, for as long as businesses have existed. Once upon a time, our organisational data was physically held in filing cabinets or piled in boxes in a dingy room in the back of the office. Back then, company data was constantly in danger of going missing, being incorrectly filed, or was at the mercy of natural disasters.
We’ve come a long way from filing cabinets and physical documents. These days, most of our data is stored on servers, hard drives, or in the cloud. But with these technological advancements, our data is now under more threat than ever. Not only do we also experience data loss due to natural disasters and incorrect filing (how many times have you thought ‘now where on earth did I save that document!?’), we must also defend against ransomware/malware attacks, accidental deletions/damage, server outages, and a whole host of other potential threats that are waiting to snatch away your data and remove it from existence, oftentimes with devastating results.
What causes data loss?
As mentioned, there are several ways your data can disappear from the ether, with the most common being:
HUMAN ERROR:
Humans make mistakes, and sometime human error can result in overwriting important files and deleting information that is essential to your business. Human error can also result in other forms of data loss such as spillage, drops, or other accidents that could damage devices/servers.
EXTERNAL SECURITY THREATS:
Viruses, malware and ransomware are the biggest threats to your data. Malware can slow down your systems, and steal or corrupt your data. Worse still, ransomware does the same with the added threat of holding your data ransom until you pay a hefty fee.
OUTAGES:
Power outages can completely halt business operations by shutting your systems and devices down without warning. This not only results in the loss of unsaved data but can also corrupt files due to improper shutdown procedures.
THEFT:
Many businesses assign laptops to their employees and allow them to take their devices with them when they leave the office. This, of course, can result in the loss or theft of company property. If their unbacked-up files on lost or stolen devices, you can say goodbye to those files forever.
How to protect your data
So how do we lessen the impact in the event of data loss? The biggest defence against human error and external threats is to BACK UP YOUR DATA. And I don’t just mean save your files on a hard drive or a USB and tuck it away into a ‘safe’ place – that solution is simply not viable for organisations storing valuable data.
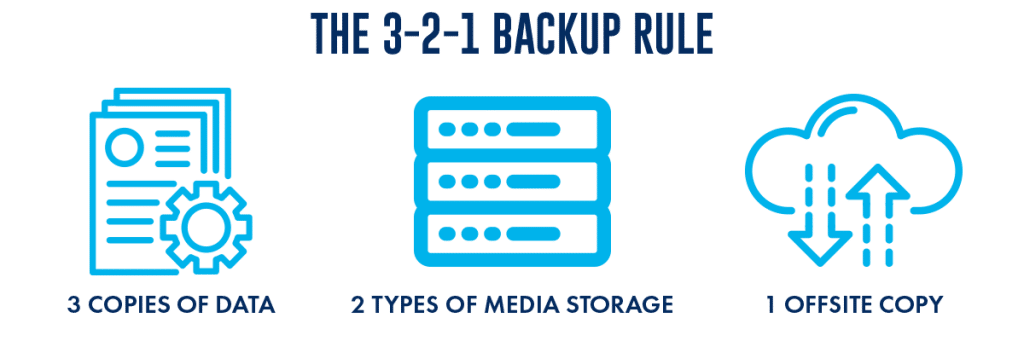
As a business owner, you absolutely need a diligent backup program with multiple backup and recovery points. This brings us to the 3-2-1 backup rule.
WHAT’S THE 3-2-1 BACKUP RULE?
The rule goes like this:
3 COPIES OF YOUR DATA
2 BACKUPS ON DIFFERENT MEDIA (for example, on your computer, external hard drive, or on-premise server)
1 BACKUP OFFSITE (e.g. in the cloud, or in an offsite server or data centre)
Following the 3-2-1 backup rule, it is advised that businesses should have both an on-premise and cloud-based backup solution.
Now let’s delve into maturity level one requirements:
Maturity Level One Requirements
Requirement 1:
Backups of important data, software and configuration settings are performed and retained in a coordinated and resilient manner in accordance with business continuity requirements.
This one is self-explanatory – you should be backing up your data regularly, with multiple disaster recovery points to fall back on in the event of malware or ransomware attacks. At the end of the day, the regularity of your backups is up to you, but as a general rule of thumb, you should make sure you are backing up your data daily and retaining your data for a period of 3 months or more.
Requirement 2:
Restoration of systems, software and important data from backups is tested in a coordinated manner as part of disaster recovery exercises.
Whether your backups are on an on-premise server or in the cloud, you should be testing the accessibility of your data regularly. In the event of a disaster, you need to be able to recover and restore your data from a period before the event occurred. Every 3 months, perform a disaster recovery exercise to ensure that your backups are working correctly and you can access files that are essential to your business.
Requirement 3:
Unprivileged accounts can only access their own backups, so obviously users who have standard user accounts should not be able to access any backups that they have not backed up themselves. This is because standard user accounts can be vulnerable to attack, so it’s best to have important backups well out of reach of your standard accounts.
Requirement 4:
Unprivileged accounts are prevented from modifying or deleting backups.
Similar to requirement 3, standard user accounts should be denied access to the settings or modifications of your backups. This is so if an adversary happens to gain access to a standard user account, they won’t be able to delete or modify your settings, thus rendering your backups useless.
Where do you start?
There’s a good chance your business already has cloud backups and on-prem backups, buti f you don’t, there are a whole host of solutions available to you.
Here are a couple of our recommendations:
- Veeam
- Barracuda
- Synology
- Or our own cloud backup solution, which can guarantee the safety of your cloud data in our Tier 3 Data Centre.
And that’s it for regular backups!
But before you go, since this is the last episode of this series, I’d like to offer everyone watching a 15% discount on eStorm’s cyber security audits and assessments. During the audit we can assess your essential eight implementation and give you detailed recommendations on how to improve your cyber security position.
Thanks for watching, and as usual, if you have any questions please feel free to contact me. Farewell, until we meet again!